I was so looking forward to a long holiday weekend but I think this is very important… important enough for a rare Saturday tip.
A virus infected email is making the rounds, purportedly from Microsoft, updating their service agreement. It looks like the real message but the URLs point to another site, typical of a phishing scheme. The real Microsoft service agreement email's links point to urls like //email.microsoft.com/Key-9850701.C.CFC8.G.KK.nCdd9Wk, which redirects to a legitimate Microsoft webpage. (I'm not going to comment about how stupid it is for Microsoft to include redirected links in email. Suffice to say, they need to use direct links in their emails.)
The infected message (or one version of it) includes an embedded external HTML file:
<img src="//{infected-site}/index.html">When you download external content, either automatically or per message, that HTML file will be saved to the hard drive and it will be rendered in Outlook. While Outlook renders HTML in the Restricted zone, it appears this week's Java exploit may be able to render the Java applet in the external file. (I'm still looking into it.)
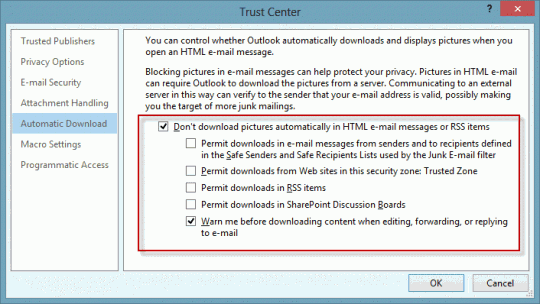
Long time subscribers should be aware of my feelings on Outlook's blocked external content settings:
Don't download external content by default.
No exceptions. Don't trust anyone.
With external content blocked by default, mail loads faster, web bugs aren't sent back to the sender and most importantly, blocking external content may prevent this java exploit from infecting your computer.
Messages sent with external content are almost always "bulk mail" – messages from advertisers and spammers. In most cases, the blocked content is a logo and style sheets, adding eye-candy but not content. You won't miss much by not downloading this content. In the case of advertisements that are all images, you can easily download the content when the message subject or text in the body is enticing enough to convince you that the blocked content is worth reading. (Take note advertisers: use more text, fewer external images!)
If you block external content *and* do not trust anyone, the HTML will not render and the Java definitely won't run.
Reading all mail in plain text is also an option. This is more effort when you need to read a message in HTML and doesn't increase security that much more than blocking external content. In a usability vs security contest, blocking external content wins on usability and is just a hair behind plain text on security.
To block external content in Outlook 2010 and 2013, go to File, Trust Center, Automatic Downloads. My recommendation: don't download any content and always warn before replies.
(If you want to read all mail in plain text, the setting is on the E-mail Security tab.)
In Outlook 2007, block content from the Tools, Trust Center menu. In Outlook 2003, the blocked external content settings are in Tools, Options, Security, Change Automatic Download Settings.
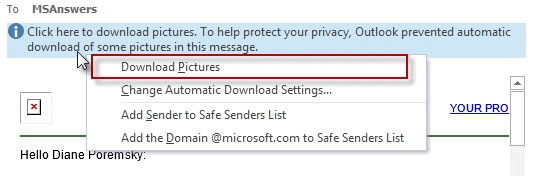
When you are reading a message and want to view the content, click on the Infobar and download external content for that message. You only need to do this once per message, Outlook will remember until the Temp Internet Cache is emptied.
Published September 1, 2012. Last updated on July 18, 2014.

![Diane Poremsky [Outlook MVP]](http://www.outlook-tips.net/images/2014/MVP_BlueOnly.png)